Terminal protection
Endpoint security is the application of solutions to protect endpoint devices such as computers, laptops, mobile phones, tablets, and devices. IoT devices and other network-connected devices. The goal of endpoint security is to prevent, detect, and respond to security threats at the endpoint

1. Mobile device protection
- Product: Mobile Security
- Company: Dream Security
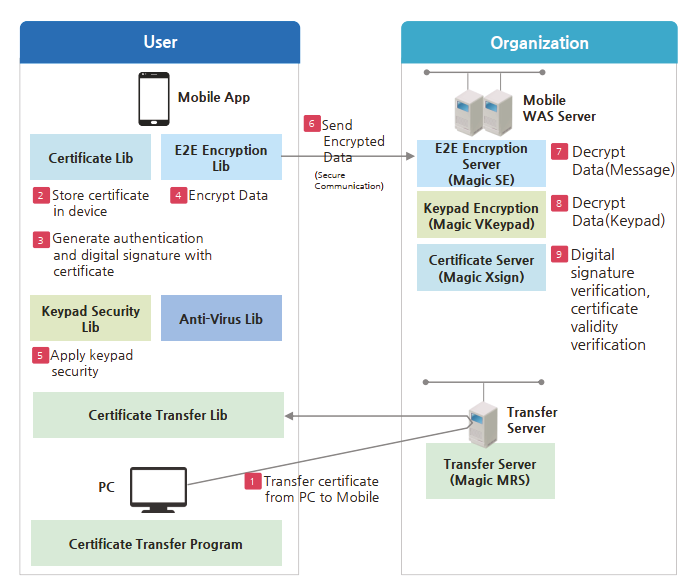
Dream Security’s Mobile Security solution provides encryption/decryption and digital signature capabilities across diverse mobile environments: Provides a mobile authentication environment dynamic optimization through certificate transfer, certificate authentication, and digital signatures.
Key solution features:
- Complies with global PKI standards.
- Includes encryption module certified to NIS standards and has passed NIS security compliance verification through public project.</li >
- Supports multiple mobile platforms including iOS, Android, blackberry, Windows Mobile/ Phone/ Metro, etc.
- Ensures fast encryption/decryption with single network transfer based on server certificate (Magic SE).
- Ensures interoperability with various client modules such as keyboard security, anti-tampering and anti-virus.
- Server Lib, developed in Pure Java, is not affected by OS/WAS version or server revision. This ensures the operational stability of the service server.
- Ensures interoperability with various client modules such as keyboard security, anti-tampering and anti-virus.
2. Protection for IOT devices:
- Product: IoT Security
- Company: Dream Security
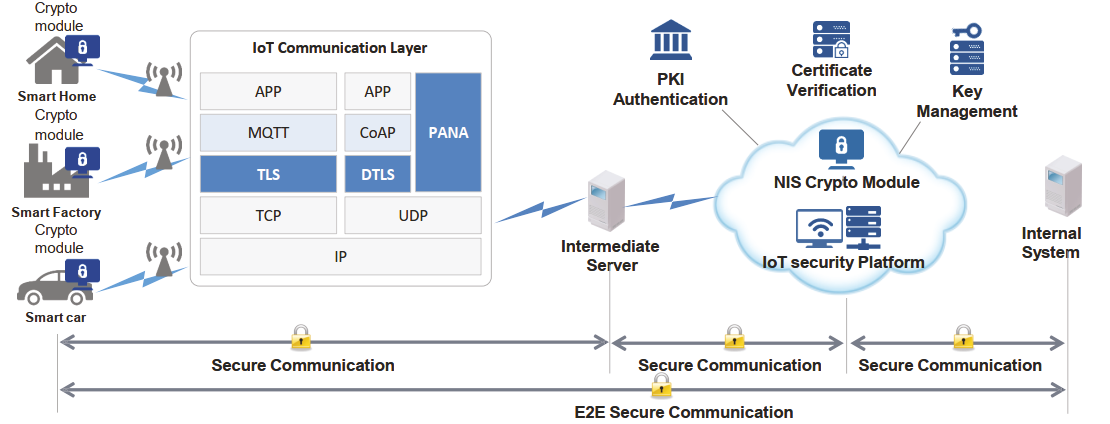
Dream Security’s IoT Security solution is the optimal security solution for IoT environments such as smart homes, factories, smart cars,…
Main features include:
- Authentication key infrastructure: PKI system for device certificate issuance (providing simple/batch certificate issuance functionality), custom SCVP system for the device’s operating environment.
- Key management system: Manage key lifecycle such as key generation, distribution, etc. suitable for IoT devices and environments.
- Secure communication: Key exchange uses the PANA protocol to ensure secure communication between devices. Secure communication using (D)TLS protocol for IoT environments using TCP/UDP.
- Encryption module: Lightweight and energy-efficient encryption algorithm for limited power and resources. Firmware-based lightweight encryption, Adopt chip-based hardware encryption module.
